Anmeldungsdatum: Aug 2007
Beiträge: 1957
|
Kategorie: Tools
Entwickler: evolution536
Beschreibung:
v3.2:
- Changed the Unknowncheats forum link in about dialog to the CrySearch website (Um Links zu sehen, musst du dich registrieren);
- Changes to the disassembler:
- Fixed bug where not all contents of some memory page would be disassembled by Capstone;
- Removed memory page selection control in favor of scrolling from page to page using up and down buttons;
- Reverted back to one background thread, threadpools and multiple threads are not necessary.
- Fixed bugs in memory scanner, resulting in certain ranges of memory not being searched at all;
- Added description of address table entry to memory dissection window where applicable;
- Added code cave scanner that identifies nop, int3 and zero sleds, accessible from the Tools menu.
- Accessing processes remotely, also system processes when running as Administrator;
- Memory scanning for primitive types, strings and byte sequences;
- Filtering scan results (a.k.a. Next scan);
- Supports relative addresses and offsets;
- Creating, saving and reusing address tables containing scan results.
- Changing values at memory addresses and freeze them;
- Viewing PE (Portable Executable) information about the opened process;
- Viewing and dumping sections;
- Viewing threads, change priority, suspend, resume and create threads remotely;
- Viewing, injecting, ejecting, dumping and hiding modules, and restore PE headers from a file on the disk;
- Allocating memory blocks remotely;
- Generating code snippets from address tables;
- Hotkeys to automate actions that do not require user input;
- Viewing import address table of loaded process and its modules;
- Settings hooks on the IAT of a process and its modules and restoring export addresses;
- Viewing PEB and TEB's for loaded process and its threads, including manipulation of certain associated information;
- Viewing and closing handles in the loaded process;
- Disassembling executable pages in a process to provide memory view and program flow control;
- Walking heaps in the opened process as side feature of the disassembler;
- Debugging executable code and data to find out what the flow of a program is;
- Plugin system featuring CrySearch extensions to be written in MASM, C or C++;
- Generate signatures and byte-arrays from selected disassembly;
- Create memory dissections of specific parts of the process' memory and save them to the address table;
- A read-only operation mode which eliminates all writing operations on a process, which is useful for evading anti-cheating systems;
- Scanning for code caves of variable sizes in accessible memory pages.
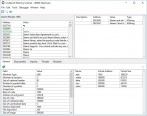
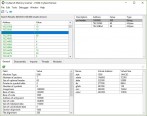
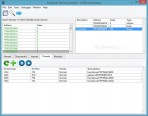
Screenshots:
Download:
CrySearch Memory Scanner - v3.2
|

 Deutsch
Deutsch English
English