|
Extreme Injector v2.1 | #1 |
|
Anmeldungsdatum: Mai 2014 Beiträge: 411 Benutzer-Bewertung: 20 positiv
11 negativ
|
Kategorie: Tools Entwickler: Master131 Beschreibung: Features: - Colourful and customizable GUI - Process List - Multi-DLL injection (with options to enable/disable DLLs to inject) - Auto-Inject - Stealth Inject - Close on inject - DLL Scrambling (scrambles DLLs on injection to make hacks harder to detect and make detected hacks work again) - 'Un-inject' DLLs - Mutiple injection methods (Standard, LdrLoadDll Stub, Thread Hijacking and Manual Map) - Drag and drop support - 64-bit injection support. How to use: - Download and extract the attachment - Run Extreme Injector v2 by master131.exe - (optional) Click Settings and then Start in Secure Mode to avoid Anti-Cheat detection of the injector itself. - Type in a process name into the box (including the extension). If you want to target a specific process or select by window name, use the Select button. - (Note) If you are injecting into Combat Arms, make sure to type in Engine.exe - Add the DLLs you want by clicking on the Add DLL button. You can also drag and drop them into the DLL list. - You can disable/enable which DLLs to inject so you can keep your favourite DLLs without needing to find them each time. - Go into Settings and customise the settings to your liking. Everything should be straight forward. - (Note) You do not need to use the "Scramble DLL" button under Tools unless you want to use a scrambled DLL with a seperate injector. The injector will automatically scramble the file before it is injected into the game. - (Note) If you are injecting into Combat Arms, make sure to tick Auto-Inject and start the game. - Click Inject and enjoy! (or wait for the process to start and let it auto-inject if you ticked auto-inject) Please explain the Injection Methods! This version of the injector introduces 2 new injection techniques. - Standard - This is the injection technique used in nearly every injector out there. It uses CreateRemoteThread and LoadLibrary and is the most reliable injection technique. - LdrLoadDll Stub - This is similar to the Standard injection technique except it goes 1 level deeper into LoadLibrary. - Thread Hijacking - This was the "Alt" injection techinique seen in the previous version. It is pretty stable and is not used by many injectors. - Manual Map - This is the most secure injection technique. So secure that even Windows won't even know about the injected DLL. This injection technique may have problems with hacks that are packed with a packer so try another method if this doesn't work. Please explain the Scramble Options! If you've used DLL Scrambler, you're probably familiar with these options. - Scramble DLL - Tick this to enable/disable DLL Scrambling completely - Scramble Header - This will scramble the area around the start of the file which should not impact the DLL at all - Remove Debug Data - This will remove a string in the DLL (as well as 'Debug Data') which Anti-Cheat vendors *could* use as a signature. - Append Random Data - This will add random data to the end of the file. - Shift Section Code - This will shift or move some of the assembly code (and other data in the DLL) using a random offset. This is good if an anti-cheat tries to search for a specific signature at a specific offset. Please explain the Post-Inject Options! These post-inject techniques are often seen within hacks to try prevent detection from anti-cheats but this injector can do it externally if the hack doesn't do it already. - Erase PE - This erases the PE headers at the start of the injected DLL, making it hard for anti-cheats to identify that a DLL exists at a specific location. - Hide Module - This hides the DLL from the process' module list so if an anti-cheat were to search through a process' module list, it would not appear. About the new 64-bit injection: That's right, this new version of Extreme Injector supports 64-bit DLLs and 64-bit processes. On a 64-bit computer, the injector runs as a 64-bit process and on a 32-bit computer, it runs as a 32-bit process. That means you can inject 64-bit hacks into 64-bit processes (don't worry, you can still inject into 32-bit processes on a 64-bit OS). There's a problem though. There are probably zero 64-bit hacks out there and there are hardly any 64-bit games. This is just a feature I decided to add for the future. For example, the next version of the Frostbite engine (used by Battlefield) will force users to have a 64-bit OS. This may be useful if 64-bit hacks were to appear. Known bugs/limitations: - Thread Hijacking is not supported at all on XP 64-bit. - 64-bit injection only supports Standard injection (if you choose another injection technique, it will automatically use the Standard one). When using 'Start in Secure Mode'.... If your anti-virus detects a threat/virus when you click on it, please ignore it or temporarily disable your anti-virus, it's a false positive. I would never infect any users with anything. Note that you should NOT add an exclusion to the Temp folder as any REAL viruses that emerge there might get through. Injection failed...? Try using another injection method, some do not work with all hacks. Requirements: Um Links zu sehen, musst du dich registrieren Screenshots: 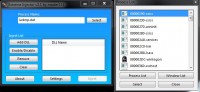 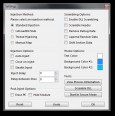 Download: Extreme Injector v2.1 __________________ AIMBOT???? I DONT SEE ANY AIMBOT  JUST SKILLS MY FRIEND!!! |
|
| Fotic ist offline | ||
|
1 positiv
0 negativ
|
Dieser Beitrag wurde bewertet von:
Jame404NotFound
(Fr 25. Dez 2015, 14:42)
|
|
 Deutsch
Deutsch English
English