Anmeldungsdatum: Aug 2007
Beiträge: 8643
Benutzer-Bewertung:
|
Kategorie: Tools
Entwickler: DarthTon
Beschreibung:
Features:
- Supports x86 and x64 processes and modules
- Injection of pure managed images without proxy dll(code was partially stolen from _Mike@OC)
- Windows 7 cross-session and cross-desktop injection
- Injection into native processes (those that only have ntdll loaded)
- Calling custom initialization routine after injection
- Unlinking module after injection
- Injection using thread hijacking
- Injection of x64 images into WOW64 process(read more in Additional notes section)
- Image manual mapping
Changelog
+ V1.1.0
- Added module view
- Module unloading
V1.0.1:
- Fixed bug with remote memory deallocation after manual mapping
- Exception handler aren't created now if process has DEP turned off.
Supported OS - Win7 - Win8.1 x64. Should also work on x86 OS versions but I haven't tested it much.
Additional notes:
Injector has 2 versions - x86 and x64. Apart from obvious features x86 version supports injection of x64 images into x64 processes; x64 injector supports injection of x86 and x64 images into WOW64 processes. However this is only valid for native images. If you want to inject pure managed dll - use same injector version as your target process is.
Injection of x64 images into WOW64 process is totally unpredictable. If you want to do this I would recommend to use manual mapping with manual imports option, because native loader is more buggy than my implementation in this case  (especially in windows 7). (especially in windows 7).
Restrictions:
- You can't inject 32 bit image into x64 process
- Use x86 version to manually map 32 bit images and x86 version to map 64 bit images
- You can't manually map pure managed images, only native injection is supported for them
- May not work properly on x86 OS versions
Manual map features:
- Relocations, import, delayed import, bound import
- Static TLS and TLS callbacks
- Security cookie
- Image manifests and SxS
- Make module visible to GetModuleHandle, GetProcAddress, etc.
- Support for exceptions in private memory under DEP
- C++/CLI images are supported (use 'Add loader reference' in this case)
Readme
Some option explanations:
Injection type:
Native inject - common approach using LoadLibraryW \ LdrLoadDll in newly created or existing thread
Manual map - manual copying image data into target process memory without creating section object
Process selection:
Either select existing non-protected process or select executable (by pressing 'New' button) that would be launched before injection into it.
Image:
Full-qualified path to image you want inject. Drag'n'drop is also supported.
Init routine:
If you are injecting native (not pure IL) image, this is name of exported function that will be called after injection is done. This export is called as void ( __stdcall* )(wchar_t*) function.
If you are injecting pure managed image, this is name of public method that will be executed using ICLRRuntimeHost::ExecuteInDefaultAppDomain.
Init argument:
String that is passed into init routine
Native Loader options:
Unlink module - after injection, unlink module from InLoadOrderModuleList, InMemoryOrderModuleList, InInitializationOrderModuleList, HashLinks and LdrpModuleBaseAddressIndex.
Context thread:
New thread - LoadLibrary and init routine will be executed in new thread.
Any other selection - LoadLibrary and init routine will be executed in the context of selected thread.
Manual map options:
Add loader reference - Insert module record into InMemoryOrderModuleList/LdrpModuleBaseAddressIndex and HashLinks. Used to make module functions (e.g. GetModuleHandle, GetProcAddress) work with manually mapped image.
Manually resolve imports - Image import and delayed import dlls will be also manually mapped instead of being loaded using LdrLoadDll.
Wipe headers - Erase module header information after injection. Also affects manually mapped imports.
Ignore TLS - Don't process image static TLS data and call TLS callbacks.
No exception support - Don't create custom exception handlers that enable out-of-image exception support under DEP.
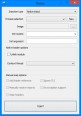
Screenshots:
Download:
Xenos_1.1.0
|


 Deutsch
Deutsch English
English (especially in windows 7).
(especially in windows 7).